Misago Unofficial-community Documentation
Tested Versions
Before You Begin
Common Notes
- You are required to utilize a unique client id for every client.
- The client id on this page is merely an example and you can theoretically use any alphanumeric string.
- You should not use the client secret in this example, We strongly recommend reading the Generating Client Secrets guide instead
Assumptions
This example makes the following assumptions:
- Application Root URL:
https://misago.example.com - Authelia Root URL:
https://auth.example.com - Client ID:
misago - Client Secret:
misago_client_secret
Configuration
Application
To configure Misago to utilize Authelia as an OpenID Connect 1.0 Provider:
- sign in to your forum's admin panel
- go to settings and click on "OAuth 2"
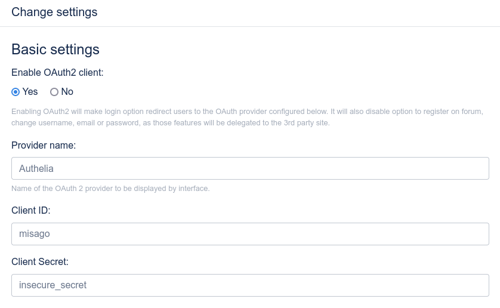
- Basic Settings (for now leave 'Enable Oauth2 Client:' set to
No)- Provider name:
authelia - Client ID:
misago - Client Secret:
misago_client_secret
- Provider name:
- Initializing Login
- Login form URL:
https://auth.example.com/api/oidc/authorization - Scopes:
openid profile email
- Login form URL:
- Retrieving access token
- Access token retrieval URL:
https://auth.example.com/api/oidc/token - Request method:
POST - JSON path to access token:
access_token
- Access token retrieval URL:
- Retrieving user data
- User data URL:
https://auth.example.com/api/oidc/userinfo - Request method:
GET - Access token location:
Query string - Access token name:
access_token
- User data URL:
- User JSON mappings
- User ID path:
sub - User name path:
name - User e-mail path:
email
- User ID path:
Save the settings and set up the authelia configuration.
Authelia
The following YAML configuration is an example Authelia client configuration for use with Misago which will operate with the above example:
for allowed origin:
identity_providers:
oidc:
allowed_origins:
- https://misago.example.com
allowed_origins_from_client_redirect_uris: true
and for the client section:
clients:
- id: misago
secret: <misago_client_secret>
public: false
authorization_policy: two_factor
scopes:
- openid
- profile
- email
redirect_uris:
- https://misago.example.com/oauth2/complete/
grant_types:
- refresh_token
- authorization_code
response_types:
- code
response_modes:
- form_post
- query
- fragment
userinfo_signing_algorithm: none
The refresh_token is not used in the authorization flow by misago, but will allow you to use a reverse proxy to only allow access to the admin panel by a user with the correct group permissions.
Restart Authelia to apply to new configuration and check for any errors in the log
Return to Application
Assuming all is well, you can return to the Misago Oauth2 Settings page, in the admin panel:
- Basic Settings:
- Enable Oauth2 Client:
Yes
- Enable Oauth2 Client:
Saving the settings should now activate Oauth2 login to Misago as a client from your Authelia instance.