Sorry but this is just NOT true.
The only authoritative part of OAuth2 is subject, which is what Misago follows and respects. Only reason why Misago associates OAuth users with emails is thay system allowing user to change their email that was done right requires user to verify e-mail ownership through link in e-mail message. Making it much more trustful as fall-back identifier than username is. But this only happens when OAuth was enabled after user already registered on a site using built in registration method. How many users like that do you have?
Misago (and many other systems like Discourse) mangles user names that don’t follow the system requirements. „John Doe” and „John_Doe” are same username because space is not allowed. „Rafał” and „Rafal” are same username because username needs to use latin alphabeth only.
Name not changing sounds like something specific to your setup. I’ll setup Facebook as my auth provider. Now I have a problem because you can change your name on Facebook no problem. I’ll setup keycloak where name can be changed as often as user wants to. Now I have problem. I’ll integrate with webstore. Now I don’t have username at all, only their e-mail address. I have a problem.
email address in misago is retained as the incorrect old email address, and there is no way for the user to change that.
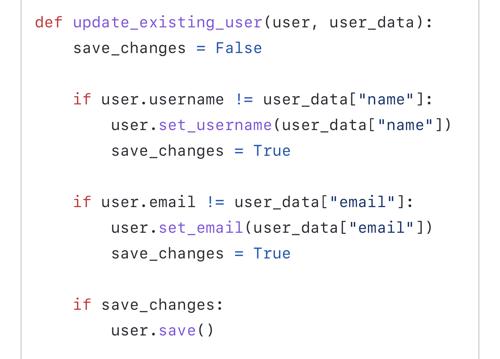
If this is the case, it is a bug in Misago and I’ll fix it.